RealNetworks, Inc. Releases Update to Address Security Vulnerabilities. In the Tools menu select Check for Update or go here to check your player.
Link to RealNetworks Update Info
Just my day to day stuff. Computers, Family and Life. Two kids in the U.S. Navy and one in the U.S. Army
Thursday, March 30, 2006
Customizing your Windows XP computer
I ran across this nice little web page from Microsoft that has several useful tips on Customizing your Windows XP computer. From screen resolution to background photos, you can make Windows XP look and work the way you want.
Check it out.
Check it out.
Some useful windows keyboard shortcuts.
Copy: CTRL+C
Cut: CTRL+X
Delete an item without sending it to the recycle bin: SHIFT+DEL
Paste: CTRL+V
Select all: CTRL+A
Start menu: CTRL+ESC (or the Windows key)
Switch between open programs: ALT+TAB
CTRL+Z (Undo.)
APPLIES TO
Microsoft Windows Millennium Edition
Microsoft Windows 98 Second Edition
Microsoft Windows 98 Standard Edition
Microsoft Windows 95
You can find more here from Micrisoft.
APPLIES TO
Microsoft Windows XP Home Edition
Microsoft Windows XP Professional
You can find more here from Microsoft.
Cut: CTRL+X
Delete an item without sending it to the recycle bin: SHIFT+DEL
Paste: CTRL+V
Select all: CTRL+A
Start menu: CTRL+ESC (or the Windows key)
Switch between open programs: ALT+TAB
CTRL+Z (Undo.)
APPLIES TO
Microsoft Windows Millennium Edition
Microsoft Windows 98 Second Edition
Microsoft Windows 98 Standard Edition
Microsoft Windows 95
You can find more here from Micrisoft.
APPLIES TO
Microsoft Windows XP Home Edition
Microsoft Windows XP Professional
You can find more here from Microsoft.
101 Fabulous Freebies
101 Fabulous Freebies
The best things in life aren't just free--they're indispensable. Case in point: these outrageously useful downloads, sites, and services. From the May 2006 issue of PC World magazine.
Click here to see the list at PC World
The best things in life aren't just free--they're indispensable. Case in point: these outrageously useful downloads, sites, and services. From the May 2006 issue of PC World magazine.
Click here to see the list at PC World
Wednesday, March 29, 2006
Outlook or Outlook Express for e-mail turn off the preview pane
If you use Outlook or Outlook Express for e-mail turn off the preview pane. Using the preview pane will make you more vulnerable to computer viruses.
Outlook and Outlook Express has had its share of security problems over the years, and there have been malicious threats that take advantage of its preview pane, which displays the contents of a message without your having to open the file.
I recommended turning off the preview pane to prevent such instant virus and worm infections when you go through your e-mail.
You can turn off the preview pane by going to the Views menu in Outlook Express or Outlook, In Outlook Express selecting the Layout option and un-checking the box next to "Show preview pane."
Outlook Express 6.0 has more security features than previous versions; you can find these settings by going to the Tools menu, to Options, and clicking on the Security tab. Here, among other settings, you can have Outlook Express block images and attachments that might contain viruses.
Outlook and Outlook Express has had its share of security problems over the years, and there have been malicious threats that take advantage of its preview pane, which displays the contents of a message without your having to open the file.
I recommended turning off the preview pane to prevent such instant virus and worm infections when you go through your e-mail.
You can turn off the preview pane by going to the Views menu in Outlook Express or Outlook, In Outlook Express selecting the Layout option and un-checking the box next to "Show preview pane."
Outlook Express 6.0 has more security features than previous versions; you can find these settings by going to the Tools menu, to Options, and clicking on the Security tab. Here, among other settings, you can have Outlook Express block images and attachments that might contain viruses.
Transfer settings from Internet Explorer to Firefox
Some people that want to switch to the Firefox web browser from Internet Explorer have asked me if they can get their Favorites list. The short answer is yes. Firefox is a free Web browser from the Mozilla Corp., and the program works on many Windows, Mac OS X and Linux systems. It can import bookmarks or favorites from several other Web browsers, including Internet Explorer, Opera and Safari, and can also bring over cookies, saved passwords and browser history files.
Once you install Firefox on your computer (www.mozilla.com), open the program and go to the File menu. Select the Import option, and a set of dialogue boxes guides you through importing your bookmarks and other data from your older browser.
Once you install Firefox on your computer (www.mozilla.com), open the program and go to the File menu. Select the Import option, and a set of dialogue boxes guides you through importing your bookmarks and other data from your older browser.
Monday, March 27, 2006
Benefits of leaving computers turned on
I had someone ask me what were the benefits of leaving their computer turned on all the time.
The biggest thing I can say is Updates. If you set your Windows and Antivirus software to update automatically and you leave your computer turned on you can accomplish the updates while you are sleeping and therefore not wasting valuable time doing it when you get up in the morning. Most lay computer users forget to do the updates themselves, ( I have personally seen computers that have had no updates done in years ).
Another benefit that I see is less thermal stress on the components when you leave your computer turned on rather than constantly turning it on and off. The constant cooling and heating of chips by powering down every night seems to wear them out faster, and the moving components like fans and Hard Drives being powered down and then turned back on each day seems to wear them out faster too.
If you are going to leave your computer turned on make sure you have a good Firewall and have good antivirus software running. Those are a must for everyone. Also make sure that you do a reboot ( or restart ), that clears up items in the computer's memory and gives it a fresh start every so often.
John
The biggest thing I can say is Updates. If you set your Windows and Antivirus software to update automatically and you leave your computer turned on you can accomplish the updates while you are sleeping and therefore not wasting valuable time doing it when you get up in the morning. Most lay computer users forget to do the updates themselves, ( I have personally seen computers that have had no updates done in years ).
Another benefit that I see is less thermal stress on the components when you leave your computer turned on rather than constantly turning it on and off. The constant cooling and heating of chips by powering down every night seems to wear them out faster, and the moving components like fans and Hard Drives being powered down and then turned back on each day seems to wear them out faster too.
If you are going to leave your computer turned on make sure you have a good Firewall and have good antivirus software running. Those are a must for everyone. Also make sure that you do a reboot ( or restart ), that clears up items in the computer's memory and gives it a fresh start every so often.
John
Windows - Explorer Shell Replacements
A great list of replacement shells for Windows. "Shell replacements take the place of the Windows Explorer. That is, they provide a substitute for the System tray, the Taskbar, the Desktop, My Computer, and/or the Start Menu. Usually the substitute is more configurable, flexible, and more attractive than the Explorer."
read more | digg story
read more | digg story
$10,000 Dell PC Sold Out!
Dell has finally launched the XPS 600 Renegade gaming PC. The machines have already sold out.
www.bloggershq.com - Community for Bloggers
read more | digg story
www.bloggershq.com - Community for Bloggers
read more | digg story
Sunday, March 26, 2006
Review of Windows media player 11
The latest version of Windows Media Player is the best yet, featuring a clean, visual interface and excellent performance that will give other jukebox apps a run for their money.
I think I'll stick with WinAmp
read more | digg story
I think I'll stick with WinAmp
read more | digg story
Sell your used books to Barnes & Noble (Shipping covered)
Sell your used books to Barnes & Noble. You can see how much they will pay for your book with ISBN look up. If you are happy with the price you can complete the transaction and they will provide you with a return label so you can send the book to them for free. After the book is received they will mail you the check.
Click here to Check it out.
Click here to Check it out.
Microsoft PowerToys for Windows XP
Good morning, I just got up and am still on my first cup of coffee. I was just thinking that in my experience most people don't know about the Power toys available for Windows XP from Microsoft. PowerToys add fun and functionality to the Windows experience. PowerToys are additional programs that developers work on after a product has been released.
Check out these websites from Micrisoft for Power Toys.
Windows XP PowerToys and Add-ins
Microsoft PowerToys for Windows XP
Check out these websites from Micrisoft for Power Toys.
Windows XP PowerToys and Add-ins
Microsoft PowerToys for Windows XP
Saturday, March 25, 2006
GNU Image Manipulation Program - Free
My son posted a comment saying that I should have mentioned GIMP in my last post. For those of you that don't know what GIMP is, it is another free image editing program. GIMP is an acronym for GNU Image Manipulation Program. It is a freely distributed program for such tasks as photo retouching, image composition and image authoring. Some nice features about GIMP are that it is open source, cross-platform, flexible and powerful. GIMP is available for free for the Linux, Mac, Unix, and Windows platforms. The downside to GIMP is that it is more difficult to learn. It close to Photoshop in the learning curve, in fact It is a good free alternative to Photoshop. :)
Click here to go to the GIMP website.
Make sure you also look for other resources about GIMP on the net, they are plentiful.
Click here to go to the GIMP website.
Make sure you also look for other resources about GIMP on the net, they are plentiful.
Great Free Image Editing Program
I was just thinking I would tell you about a great free image editing program that has been around for a few years. It's called Irfanview. Irfanview is a fast and simple image viewer and editor that supports all major graphic formats, including BMP, DIB, JPEG, GIF, animated GIF, PNG, PCX, multipage TIFF, and TGA. Just be careful, upon installation, the program attempts to install two Google programs, but if you don't want them, you can choose to opt out.
Overall it's an excellent free program to view and edit images.
You can read more about it and get it here.
Irfanview Website
Make sure you go to their website and get the plugins.
Overall it's an excellent free program to view and edit images.
You can read more about it and get it here.
Irfanview Website
Make sure you go to their website and get the plugins.
Friday, March 24, 2006
The $10,000 Dell PC

STARTING at $9930, the PC has a Pentium Extreme Edition processor that has been overclocked from 3.73 to 4.26 GHz, 2GB DDR2-667 memory, a 160 GB 10,000 RPM WD Raptor as well as a second WD 400 GB 7200 RPM hard drive. PC also comes with a FOUR GeForce 7900 GTX graphics processors with a total of 2 GB of GDDR3 memory.
read more | digg story
Thursday, March 23, 2006
Clear Cache Feature for Internet Explorer
Here is a neat little program from Microsoft for all you IE users. It adds a Clear Cache Feature to Internet Explorer Click here to get it.
Erase and Reuse CD-RW disc - Tip
If you have a Windows XP computer that has a CD-RW (re-writable) discs, then you can easily erase and reuse the CD-RW disc.
1. Place the CD-RW disc you would like to reuse in your CD-RW drive.
2. Go to Start>> My Computer
3. In My Computer, right-click the CD-RW drive, and then click Open.
A temporary storage area is now displayed. This storage area is where files are held before they are copied to the CD. You will find the files listed in the "Files Ready to Be Written to the CD" box.
4. In the CD Writing Tasks pane, click "Erase this CD-RW".
Windows will now display the "Welcome to the CD Writing Wizard".
5. Click Next. The "Erasing the CD" dialog box is displayed along with a progress bar.
6. When the process is completed, you will receive a message in the notification area. You can now reuse your CD-RW disc.
1. Place the CD-RW disc you would like to reuse in your CD-RW drive.
2. Go to Start>> My Computer
3. In My Computer, right-click the CD-RW drive, and then click Open.
A temporary storage area is now displayed. This storage area is where files are held before they are copied to the CD. You will find the files listed in the "Files Ready to Be Written to the CD" box.
4. In the CD Writing Tasks pane, click "Erase this CD-RW".
Windows will now display the "Welcome to the CD Writing Wizard".
5. Click Next. The "Erasing the CD" dialog box is displayed along with a progress bar.
6. When the process is completed, you will receive a message in the notification area. You can now reuse your CD-RW disc.
The Windows logo key -Tip
The Windows logo key, located in the bottom row of most computer keyboards to the right and left of the space bar, is not used by most people. Don't ignore it. It is the shortcut anchor for the following commands:
Windows: Display the Start menu
Windows + D: Minimize or restore all windows
Windows + E: Display Windows Explorer
Windows + F: Display Search for files
Windows + L: Lock the workstation
Windows + M: Minimize all windows
Windows + Q: Quick switching of users (Powertoys only)
Windows + Q: Hold Windows Key, then tap Q to scroll thru the different users on your pc
Windows + R: Display Run dialog box
Windows + U: Open Utility Manager
Windows + Ctrl + F: Display Search for computer
Windows + F1: Display Help and Support Center
Windows + Pause/ Break: Display System Properties dialog box
Windows + Shift + M: Undo minimize all windows
Windows + Tab: Cycles through all open programs and taskbar buttons. Press [ENTER] to select.
If I missed something else let me know and I will post it here
Windows: Display the Start menu
Windows + D: Minimize or restore all windows
Windows + E: Display Windows Explorer
Windows + F: Display Search for files
Windows + L: Lock the workstation
Windows + M: Minimize all windows
Windows + Q: Quick switching of users (Powertoys only)
Windows + Q: Hold Windows Key, then tap Q to scroll thru the different users on your pc
Windows + R: Display Run dialog box
Windows + U: Open Utility Manager
Windows + Ctrl + F: Display Search for computer
Windows + F1: Display Help and Support Center
Windows + Pause/ Break: Display System Properties dialog box
Windows + Shift + M: Undo minimize all windows
Windows + Tab: Cycles through all open programs and taskbar buttons. Press [ENTER] to select.
If I missed something else let me know and I will post it here
Windows Tip... Error Reporting
Do you ever get tired of the Error Reporting in Windows XP? If you answer yes do the following.
Start the System Configuration Utility:
Click Start, and then click Run.
Type msconfig to open the System Configuration Utility.
Click the Services tab.
Clear the Error Reporting Service check box, and then click OK.
Hit Restart to reboot your system.
Your computer will now start without loading the error reporting service.
Start the System Configuration Utility:
Click Start, and then click Run.
Type msconfig to open the System Configuration Utility.
Click the Services tab.
Clear the Error Reporting Service check box, and then click OK.
Hit Restart to reboot your system.
Your computer will now start without loading the error reporting service.
Wednesday, March 22, 2006
Spyware protection for free
Windows Defender (Beta 2) is a free program that helps protect your computer against pop-ups, slow performance, and security threats caused by spyware and other unwanted software. It features Real-Time Protection, a monitoring system that recommends actions against spyware when it's detected, and a new streamlined interface that minimizes interruptions and helps you stay productive
Click here to get it from Microsoft.
Click here to get it from Microsoft.
Video: New version of the Firefox browser
New version of the Firefox browser. CNET's Robert Vamosi takes you on a visual tour of the newest version of Firefox. This is an alpha of 2.0, so this is a preview of a browser you can use now. There's no guarantee of stability, and your extensions may fail.
Click here to View the Video on Cnet
Click here to View the Video on Cnet
Microsoft delays launch of Vista
Microsoft plans to delay the consumer launch of its much-anticipated Windows Vista operating system to January 2007.
It had originally aimed to launch Vista - the first major update since Windows XP was introduced five years ago - in the second half of 2006.
Now, a version will be available for corporate customers from November 2006.
Vista will then be rolled out for consumers after the holiday shopping season, said a spokesman for Microsoft - the world's biggest software maker.
It had originally aimed to launch Vista - the first major update since Windows XP was introduced five years ago - in the second half of 2006.
Now, a version will be available for corporate customers from November 2006.
Vista will then be rolled out for consumers after the holiday shopping season, said a spokesman for Microsoft - the world's biggest software maker.
How to use MSCONFIG
Built into Windows 98, 98SE, ME, and XP is a special tool called the "Microsoft System Configuration Utility" or "MSCONFIG." Designed to help you troubleshoot problems with your computer, MSCONFIG can also be used to ensure that your computer boots faster and crashes less.
Most people know that the more programs you have running on your computer at once, the more likely it is that your computer will either run slowly or even crash.
What most people don't know is that every time you boot your computer a whole bunch of "hidden" programs load in the background. Some of these hidden programs are essential, but most aren't. Turning off some of these hidden programs can significantly increase your computer's performance and reliability.
Go to: Start
Then: Run
Type MSCONFIG in the "Open:" box and then either press enter on your keyboard or click on the OK button.
This launches Microsoft's System Configuration Utility. Click on the Startup tab (the tab at the far right).
If you use Windows XP, you'll notice that the Microsoft System Configuration Utility screen looks a little different than the one in Windows 98, 98 SE, or ME. But it still works the same. Click on the Startup tab (the tab at the far right).
This takes you to a page with a list of "startup items." Startup items are programs that are automatically loaded every time you turn on your computer. Some startup programs are absolutely necessary, others are simply a waste of memory.
The only startup items you absolutely need are:
ScanRegistry
TaskMonitor
SystemTray
LoadPowerProfile
Your antivirus program, you won't have a hard time figuring out which one is your antivirus program. It should be pretty obvious.
Since you need these startup items to be running all the time in order for your computer to work properly, make sure there is always a check mark next to all of these startup items.
If you don't see one or two these items in your list of startup items, that's ok. For example, some people may not have a LoadPowerProfile while others may have two. The big thing to remember is that you don't want to uncheck any of these files if you have them.
The rest of the startup items are completely optional. Whether you leave these optional startup items on or turn them off is completely up to you.
A good rule of thumb is to disable only those programs that you recognize and don't need to have running all the time.
When in doubt, leave it on.
Check out Paul Collins huge "Startup Applications" list at http://www.sysinfo.org/startuplist.php
Remember, disable only those programs that you recognize and don't need to have running all the time. When in doubt, leave it on.
In Windows XP, all of Windows essential programs are loaded through something called "Windows Services." This means that most of the startup items you see in XP are completely optional and can be turned off. Still, disable only those programs that you recognize and don't need to have running al the time. When in doubt, leave it on.
When you are done
Click on the OK button.
A message will pop up telling you that you must restart your computer before these changes will take effect. Click on "Yes" and your computer will automatically reboot.
If you have Windows NT or 2000, you can download the official, Windows XP version of MSCONFIG at The Tech Guide
Most people know that the more programs you have running on your computer at once, the more likely it is that your computer will either run slowly or even crash.
What most people don't know is that every time you boot your computer a whole bunch of "hidden" programs load in the background. Some of these hidden programs are essential, but most aren't. Turning off some of these hidden programs can significantly increase your computer's performance and reliability.
Go to: Start
Then: Run
Type MSCONFIG in the "Open:" box and then either press enter on your keyboard or click on the OK button.
This launches Microsoft's System Configuration Utility. Click on the Startup tab (the tab at the far right).
If you use Windows XP, you'll notice that the Microsoft System Configuration Utility screen looks a little different than the one in Windows 98, 98 SE, or ME. But it still works the same. Click on the Startup tab (the tab at the far right).
This takes you to a page with a list of "startup items." Startup items are programs that are automatically loaded every time you turn on your computer. Some startup programs are absolutely necessary, others are simply a waste of memory.
The only startup items you absolutely need are:
ScanRegistry
TaskMonitor
SystemTray
LoadPowerProfile
Your antivirus program, you won't have a hard time figuring out which one is your antivirus program. It should be pretty obvious.
Since you need these startup items to be running all the time in order for your computer to work properly, make sure there is always a check mark next to all of these startup items.
If you don't see one or two these items in your list of startup items, that's ok. For example, some people may not have a LoadPowerProfile while others may have two. The big thing to remember is that you don't want to uncheck any of these files if you have them.
The rest of the startup items are completely optional. Whether you leave these optional startup items on or turn them off is completely up to you.
A good rule of thumb is to disable only those programs that you recognize and don't need to have running all the time.
When in doubt, leave it on.
Check out Paul Collins huge "Startup Applications" list at http://www.sysinfo.org/startuplist.php
Remember, disable only those programs that you recognize and don't need to have running all the time. When in doubt, leave it on.
In Windows XP, all of Windows essential programs are loaded through something called "Windows Services." This means that most of the startup items you see in XP are completely optional and can be turned off. Still, disable only those programs that you recognize and don't need to have running al the time. When in doubt, leave it on.
When you are done
Click on the OK button.
A message will pop up telling you that you must restart your computer before these changes will take effect. Click on "Yes" and your computer will automatically reboot.
If you have Windows NT or 2000, you can download the official, Windows XP version of MSCONFIG at The Tech Guide
Booting without Windows XP logo
To do this: Click:
Click on: Start
Click on: Start
Then: Run
Type in: msconfig
Click ok
Click on BOOT.INI tab and put a tick mark against the /NOGUIBOOT option;click Apply/OK.
Restart the machine.
Click on BOOT.INI tab and put a tick mark against the /NOGUIBOOT option;click Apply/OK.
Restart the machine.
Command-line reference A-Z
To see what is available for Windows XP command line you can launch the Command-line reference A-Z list by doing the following:
Click Start
Click Run
Put the following in the run dialog box:
hh.exe ms-its:C:\WINDOWS\Help\ntcmds.chm::/ntcmds.htm
Click Ok
This will open the Command-line reference A-Z help box.
John
Click Start
Click Run
Put the following in the run dialog box:
hh.exe ms-its:C:\WINDOWS\Help\ntcmds.chm::/ntcmds.htm
Click Ok
This will open the Command-line reference A-Z help box.
John
Tuesday, March 21, 2006
Take an inventory of your computer
The Belarc Advisor builds a detailed profile of your installed software and hardware, missing Microsoft hotfixes, anti-virus status, CIS (Center for Internet Security) benchmarks, and displays the results in your Web browser. All of your PC profile information is kept private on your PC and is not sent to any web server. You can get it here.
http://www.belarc.com/free_download.html
I have been using it for years.
http://www.belarc.com/free_download.html
I have been using it for years.
All this talk about computer memory
In all this talk about computer memory this morning I though I would post this info.
My Sons Computer is a Dell Dimension 4600, Pentium 4-2.4Ghz with 512megs of PC 3200 400MHz DDR Ram, 8 USB 2.0 ports, two in the front and six in the back, two Hard Drives an 80 GB Western Digital and a 40 GB Seagate, NVIDIA GeForce FX 5200 Ultra video card with 128megs video memory, USB Wireless Optical Mouse and Keyboard, Dell 17in Flat panel LCD monitor, Video Camera, Wireless headphones, DVD player, CD/RW, and Creative SBS 5.1 560 surround sound speakers with Subwoofer connected to the internet through a super high speed cable modem.
In all that doesn't sound too bad does it? But remember he is a teenager. He really needs more computer memory, at least 1 gig to be able to run all the applications that he uses.
My Sons Computer is a Dell Dimension 4600, Pentium 4-2.4Ghz with 512megs of PC 3200 400MHz DDR Ram, 8 USB 2.0 ports, two in the front and six in the back, two Hard Drives an 80 GB Western Digital and a 40 GB Seagate, NVIDIA GeForce FX 5200 Ultra video card with 128megs video memory, USB Wireless Optical Mouse and Keyboard, Dell 17in Flat panel LCD monitor, Video Camera, Wireless headphones, DVD player, CD/RW, and Creative SBS 5.1 560 surround sound speakers with Subwoofer connected to the internet through a super high speed cable modem.
In all that doesn't sound too bad does it? But remember he is a teenager. He really needs more computer memory, at least 1 gig to be able to run all the applications that he uses.

Common Memory Types
SRAM
Static random access memory uses multiple transistors, typically four to six, for each memory cell but doesn't have a capacitor in each cell. It is used primarily for cache.
DRAM
Dynamic random access memory has memory cells with a paired transistor and capacitor requiring constant refreshing.
FPM DRAM
Fast page mode dynamic random access memory was the original form of DRAM. It waits through the entire process of locating a bit of data by column and row and then reading the bit before it starts on the next bit. Maximum transfer rate to L2 cache is approximately 176 MBps.
EDO DRAM
Extended data-out dynamic random access memory does not wait for all of the processing of the first bit before continuing to the next one. As soon as the address of the first bit is located, EDO DRAM begins looking for the next bit. It is about five percent faster than FPM. Maximum transfer rate to L2 cache is approximately 264 MBps.
SDRAM
Synchronous dynamic random access memory takes advantage of the burst mode concept to greatly improve performance. It does this by staying on the row containing the requested bit and moving rapidly through the columns, reading each bit as it goes. The idea is that most of the time the data needed by the CPU will be in sequence. SDRAM is about five percent faster than EDO RAM and is the most common form in desktops today. Maximum transfer rate to L2 cache is approximately 528 MBps.
DDR SDRAM
Double data rate synchronous dynamic RAM is just like SDRAM except that is has higher bandwidth, meaning greater speed. Maximum transfer rate to L2 cache is approximately 1,064 MBps (for DDR SDRAM 133 MHZ).
RDRAM
Rambus dynamic random access memory is a radical departure from the previous DRAM architecture. Designed by Rambus, RDRAM uses a Rambus in-line memory module (RIMM), which is similar in size and pin configuration to a standard DIMM. What makes RDRAM so different is its use of a special high-speed data bus called the Rambus channel. RDRAM memory chips work in parallel to achieve a data rate of 800 MHz, or 1,600 MBps. Since they operate at such high speeds, they generate much more heat than other types of chips. To help dissipate the excess heat Rambus chips are fitted with a heat spreader, which looks like a long thin wafer. Just like there are smaller versions of DIMMs, there are also SO-RIMMs, designed for notebook computers.
Static random access memory uses multiple transistors, typically four to six, for each memory cell but doesn't have a capacitor in each cell. It is used primarily for cache.
DRAM
Dynamic random access memory has memory cells with a paired transistor and capacitor requiring constant refreshing.
FPM DRAM
Fast page mode dynamic random access memory was the original form of DRAM. It waits through the entire process of locating a bit of data by column and row and then reading the bit before it starts on the next bit. Maximum transfer rate to L2 cache is approximately 176 MBps.
EDO DRAM
Extended data-out dynamic random access memory does not wait for all of the processing of the first bit before continuing to the next one. As soon as the address of the first bit is located, EDO DRAM begins looking for the next bit. It is about five percent faster than FPM. Maximum transfer rate to L2 cache is approximately 264 MBps.
SDRAM
Synchronous dynamic random access memory takes advantage of the burst mode concept to greatly improve performance. It does this by staying on the row containing the requested bit and moving rapidly through the columns, reading each bit as it goes. The idea is that most of the time the data needed by the CPU will be in sequence. SDRAM is about five percent faster than EDO RAM and is the most common form in desktops today. Maximum transfer rate to L2 cache is approximately 528 MBps.
DDR SDRAM
Double data rate synchronous dynamic RAM is just like SDRAM except that is has higher bandwidth, meaning greater speed. Maximum transfer rate to L2 cache is approximately 1,064 MBps (for DDR SDRAM 133 MHZ).
RDRAM
Rambus dynamic random access memory is a radical departure from the previous DRAM architecture. Designed by Rambus, RDRAM uses a Rambus in-line memory module (RIMM), which is similar in size and pin configuration to a standard DIMM. What makes RDRAM so different is its use of a special high-speed data bus called the Rambus channel. RDRAM memory chips work in parallel to achieve a data rate of 800 MHz, or 1,600 MBps. Since they operate at such high speeds, they generate much more heat than other types of chips. To help dissipate the excess heat Rambus chips are fitted with a heat spreader, which looks like a long thin wafer. Just like there are smaller versions of DIMMs, there are also SO-RIMMs, designed for notebook computers.
How Much Computer Memory /RAM Is Enough ?
The answer to this question is a straightforward...it depends. It depends upon what you are using your computer for and what operating system you are using, to take the two most obvious factors. If you are using memory intensive photo editing programs or doing video editing all the time, and want to be able to run office applications, and surf the internet, and do email, all at once - well, then you may need a fair amount of memory. If you are a typical home user and mostly use your computer for email, surfing, a word processor or spreadsheet, and the occasional game, then you won't need quite as much. In terms of how it affects you, having the right amount of memory equals a faster computer.
Here's some general guidelines for the typical home user (note MB = Megabyte, Gig = Gigabyte or 1024 MB, the main unit in terms of which memory is sold is the MB; the higher the number, the more memory you have)
Windows 95 - Seems to be happy with 64 MB. Anything over doesn't get you much performance increase, but if you have anything less, You should seriously consider getting more memory. The benefit can be quite substantial.
Windows 98/Me - Seems to be happy with 128 MB. Works semi ok with 64 MB, but you will probably see a significant performance increase by going to 128 MB. Anything over 256 MB generally doesn't get you much.
Windows 2000 - At least 128 MB, and basically as much as you can throw at it. Seriously consider 256 MB or more if it's got a heavy demand on it.
Windows XP - Hard to say, but 256 MB minimum just to run the basic apps, and definitely works better with 512 MB, and almost certainly would work better with more. I recommend 1 Gig of Ram for XP.
It's been said that you can never have enough memory. :) That's my motto
Some good information from Crucial Technology
http://www.crucial.com/library/howmuch.asp
Here's some general guidelines for the typical home user (note MB = Megabyte, Gig = Gigabyte or 1024 MB, the main unit in terms of which memory is sold is the MB; the higher the number, the more memory you have)
Windows 95 - Seems to be happy with 64 MB. Anything over doesn't get you much performance increase, but if you have anything less, You should seriously consider getting more memory. The benefit can be quite substantial.
Windows 98/Me - Seems to be happy with 128 MB. Works semi ok with 64 MB, but you will probably see a significant performance increase by going to 128 MB. Anything over 256 MB generally doesn't get you much.
Windows 2000 - At least 128 MB, and basically as much as you can throw at it. Seriously consider 256 MB or more if it's got a heavy demand on it.
Windows XP - Hard to say, but 256 MB minimum just to run the basic apps, and definitely works better with 512 MB, and almost certainly would work better with more. I recommend 1 Gig of Ram for XP.
It's been said that you can never have enough memory. :) That's my motto
Some good information from Crucial Technology
http://www.crucial.com/library/howmuch.asp
IE 7 Beta 2 Preview has been Released
IE 7 Beta 2 Preview has been Released. The software should not be used on production systems in mission-critical environments. Internet Explorer 7 Beta 2 Preview - released on March 20th - will only run on Windows XP Service Pack 2 (SP2) systems, but will ultimately be available for Windows Vista, Windows XP Professional x64 Edition, and Windows Server 2003. Get your copy today.
John
John
Monday, March 20, 2006
How much Memory will you really need for Vista?
Baseline Windows Vista offerings will require 512MB of DRAM just to install, with a 1GB recommendation -- but there is more to this story.
read more | digg story
read more | digg story
How-To Announce Your New Web Site
The purpose of this FAQ is to help show you how to publicize your new Web site. Although there are many sites listed here, the purpose is not to show you where. If you follow the hints and guidelines below you will certainly increase you readership.
read more | digg story
read more | digg story
New World Record in Tornado Survival
This man may hold the record for the longest distance traveled by anyone picked up by a tornado who lived to tell about it. "I've never heard of anyone going that far in a tornado and surviving," said Tom Grazulis, a Vermont-based tornado researcher.
read more | digg story
read more | digg story
A New Google Toolbar Made Especially For Firefox Users!!!
Are You Tired Of The Current Design Of The Google Toolbar? Do You Have Firefox? If You Answered Yes, Then This Is Perfect For You. Google Fans Made This Open Source Toolbar Just Fro Firefox Users. Go Check It Out.
read more | digg story
read more | digg story
10 "Intermediate" Ways To Speed Up Windows
Follow up to a nice, previous tutorial: 10 Simple Ways To Speed Up Windows XP that really helps!! Link
read more | digg story
read more | digg story
Sunday, March 19, 2006
And The Survey Says
Survey shows Firefox is Best Browser, and Opera Coming to Nintendo. That's right Firefox is the best web browser, even though my son might not agree. He is an Opera fan. :)
Foldershare bought by Microsoft - Now free!
My son got home from camping at 9:30am, he was wet and dirty but said he had a great time. :)
In computer news, Foldershare bought by Microsof is part of the Windows Live suite.
You can use Foldershare synchronized between linked computers, so you are always accessing the latest documents, photos, and files.
Its now free too with a Mac OS X client to boot.
https://www.foldershare.com/
In computer news, Foldershare bought by Microsof is part of the Windows Live suite.
You can use Foldershare synchronized between linked computers, so you are always accessing the latest documents, photos, and files.
Its now free too with a Mac OS X client to boot.
https://www.foldershare.com/
You get what you pay for.
I spent some time last week helping a guy that bought a Dell computer a few months ago. He didn't ask for any advice when he bought it, too bad. His hard drive failed last week, the good news is that Dell sent him a new one within 24hrs. The bad news has to do with his computer in general. He bought a Dell Dimension with a celeron processor, on board video and audio and a whopping 256 megs of memory, LOL. He is on Earthlink dialup and is running Windows XP home. Poor guy. After reinstalling the operating system and all the programs for him his computer was just barely crawling. I wished he would have talked to me before he bought that. I have always liked Dell and never really had a problem with them in general. But the old adage " you get what you pay for" is true. Oh well. I am trying to talk him into getting more memory ( at least a 1 gig ) Hopefully he will listen. :)
John
John
Teenagers
I woke up this morning at 4:30am. I really didn't have plans to get up that early but our dog Tanner thought differently. He needed out... I took a look at our weather ( rainy and cold ) and then thought about my son and a bunch of his friends. They are out camping in this. The left yesterday at about 4pm and are supposed to come home sometime today, I am sure all wet and cold... Idiots :). Live and learn... This is their Spring Break.
Amazing IE/Firefox Extension by MIT startup SiteAdvisor for Web safety
After removing tons of Spyware and junk from peoples computers I thought I would share this. SiteAdvisor is testing all Web sites for spam, spyware, & safety threats. You browse and search as normal and their empirical data (green=good, yellow=caution, red=bad) appears in an icon in IE or Firefox & next to results in Google, Yahoo, & MSN. Every site gets its own site details page w/ in-depth analysis. Take a look. http://www.siteadvisor.com/
read more | digg story
read more | digg story
Opera passes the Acid2 test!
Opera is now passing the Acid2 test in their latest weekly release. If you want to download the Opera Web Browser just go to http://www.opera.com/ It is a great Browser.
read more | digg story
read more | digg story
Dell denies Alienware acquisition
According to CNET.com.au, Dell has effectively denied rumours that it's acquired rival PC vendor Alienware, suggesting that all speculation should be taken "with a grain of salt".
read more | digg story
read more | digg story
Saturday, March 18, 2006
Google tells blogspot user he can't put msn search on his blog
Google has emailed a blogger user informing him that putting an MSN search box on his blogspot.com account is against their terms of service. Apparently adding a search box is "obstructing Googles services from operating efficiently and effectively"
read more | digg story
read more | digg story
Friday, March 17, 2006
Breakfast Casserole
I made this last night for dinner, it turned out great. I still have lots of leftovers for today. You can add other things to the recipe like green peppers :)
Breakfast Casserole
1 lb Sausage
1 lb Bacon or one jar Real Bacon bits
1 Large onion
9 Eggs
1 cup Milk
5 Cups Frozen Hash Browns ( Thawed )
3 1/2 Cups Shredded Cheddar Cheese
Salt & Pepper to taste
Cook Sausage and onion together and drain all grease. Cook Bacon and drain all grease.
Mix remaining ingredients in large bowl reserving 1/2 cup of the cheddar cheese, add the cooked Sausage and Bacon then poor into a greased 13x9 pan and bake at 350 degrees for 45 minutes or until knife inserted in center comes out clean. Add remaining 1/2 cup cheese to top and just cook until melted, about 5 min. Remove from oven and let it sit for 10 min before serving.
Breakfast Casserole
1 lb Sausage
1 lb Bacon or one jar Real Bacon bits
1 Large onion
9 Eggs
1 cup Milk
5 Cups Frozen Hash Browns ( Thawed )
3 1/2 Cups Shredded Cheddar Cheese
Salt & Pepper to taste
Cook Sausage and onion together and drain all grease. Cook Bacon and drain all grease.
Mix remaining ingredients in large bowl reserving 1/2 cup of the cheddar cheese, add the cooked Sausage and Bacon then poor into a greased 13x9 pan and bake at 350 degrees for 45 minutes or until knife inserted in center comes out clean. Add remaining 1/2 cup cheese to top and just cook until melted, about 5 min. Remove from oven and let it sit for 10 min before serving.
Thursday, March 16, 2006
Free Internet TV Service from AOL
I just read about the new Free Internet TV Service from AOL. I don't really like AOL that much but this is kinda neat and so I thought I would share it with you. The shows are free to anyone with high-speed Internet access. The network is supported through advertising. It began yesterday with 30 series, including "Growing Pains" and "Eight is Enough." The network will also offer games, polls and other interactive features. Eventually AOL plans to offer more than 100 series and at least 300 episodes per month to lure broadband users to the AOL Web site.
http://television.aol.com/in2tv
http://television.aol.com/in2tv
Run System Restore from the command line
Someone asked me how to run system restore from the command line. To do that Click on the windows key on the keyboard ( there are two of those, one to the right, and one to the left of the space bar ) and the R key to bring up the Run dialog box. You can also click on Start / then Run. Type %systemroot%\system32\restore\rstrui.exe into the run dialog box and click Enter.
If you have problems on initial boot.
1. Restart your system
2. When the system first boots, type F8 to bring up the boot menu
3. Select the Safe Mode with Command Prompt option
4. Log-on as administrator if needed
5. At your command prompt type
%systemroot%\system32\restore\rstrui.exe
6. Hit Enter 6. This will open the system restore wizard...
OTHER SYMPTOMS
System Restore tab may be missing in My Computer Properties. Also, when you start System Restore (rstrui.exe), you receive this message:
"System Restore has been turned off by group policy. To turn on System Restore, contact your domain Administrator."
-or-
System Restore Properties page says disabled by Group Policy
RESOLUTION
Click Start, Run and type REGEDIT and press Enter
Navigate to the following key:
HKEY_LOCAL_MACHINE \ Software \ Policies \ Microsoft \ Windows NT \ SystemRestore
In the right-pane:
Delete the value DisableConfig
Delete the value DisableSR
For Windows XP Professional, you can accomplish the above using Group Policy Editor as well.
Click Start, Run and type GPEDIT.MSC
Navigate to this path:
=> Computer Configuration==> Administrative Templates===> System====> System Restore
Set Turn off System Restore to Not Configured
Set Turn off Configuration to Not Configured
More Information
Turn off System Restore corresponds to DisableSR registry value. With this Policy is turned ON, the System Restore tab may be missing in My Computer Properties. Also, when you run System Restore (rstrui.exe), you receive this message:
System Restore has been turned off by group policy. To turn on System Restore, contact your domain Administrator.
Turn off Configuration corresponds to DisableConfig registry value. With this Policy turned ON, the System Restore tab will remain displayed but the user cannot configure the SR options. It reads disabled by Group Policy
If you have problems on initial boot.
1. Restart your system
2. When the system first boots, type F8 to bring up the boot menu
3. Select the Safe Mode with Command Prompt option
4. Log-on as administrator if needed
5. At your command prompt type
%systemroot%\system32\restore\rstrui.exe
6. Hit Enter 6. This will open the system restore wizard...
OTHER SYMPTOMS
System Restore tab may be missing in My Computer Properties. Also, when you start System Restore (rstrui.exe), you receive this message:
"System Restore has been turned off by group policy. To turn on System Restore, contact your domain Administrator."
-or-
System Restore Properties page says disabled by Group Policy
RESOLUTION
Click Start, Run and type REGEDIT and press Enter
Navigate to the following key:
HKEY_LOCAL_MACHINE \ Software \ Policies \ Microsoft \ Windows NT \ SystemRestore
In the right-pane:
Delete the value DisableConfig
Delete the value DisableSR
For Windows XP Professional, you can accomplish the above using Group Policy Editor as well.
Click Start, Run and type GPEDIT.MSC
Navigate to this path:
=> Computer Configuration==> Administrative Templates===> System====> System Restore
Set Turn off System Restore to Not Configured
Set Turn off Configuration to Not Configured
More Information
Turn off System Restore corresponds to DisableSR registry value. With this Policy is turned ON, the System Restore tab may be missing in My Computer Properties. Also, when you run System Restore (rstrui.exe), you receive this message:
System Restore has been turned off by group policy. To turn on System Restore, contact your domain Administrator.
Turn off Configuration corresponds to DisableConfig registry value. With this Policy turned ON, the System Restore tab will remain displayed but the user cannot configure the SR options. It reads disabled by Group Policy
Debunking Some Common Myths
I am just drinking my first cup of coffee for the day and I was reading the news and thought I would post this information from the Computer Emergency Readiness Team (US-CERT)
Debunking Some Common Myths
There are some common myths that may influence your online security practices. Knowing the truth will allow you to make better decisions about how to protect yourself.
How are these myths established?
There is no one cause for these myths. They may have been formed because of a lack of information, an assumption, knowledge of a specific case that was then generalized, or some other source. As with any myth, they are passed from one individual to another, usually because they seem legitimate enough to be true.
Why is it important to know the truth?
While believing these myths may not present a direct threat, they may cause you to be more lax about your security habits. If you are not diligent about protecting yourself, you may be more likely to become a victim of an attack.
What are some common myths, and what is the truth behind them?
Myth: Anti-virus software and firewalls are 100% effective. Truth: Anti-virus software and firewalls are important elements to protecting your information (see Understanding Anti-Virus Software and Understanding Firewalls for more information). However, neither of these elements are guaranteed to protect you from an attack. Combining these technologies with good security habits is the best way to reduce your risk.
Myth: Once software is installed on your computer, you do not have to worry about it anymore. Truth: Vendors may release patches or updated versions of software to address problems or fix vulnerabilities (see Understanding Patches for more information). You should install the patches as soon as possible; some software even offers the option to obtain updates automatically. Making sure that you have the latest virus definitions for your anti-virus software is especially important.
Myth: There is nothing important on your machine, so you do not need to protect it. Truth: Your opinion about what is important may differ from an attacker's opinion. If you have personal or financial data on your computer, attackers may be able to collect it and use it for their own financial gain. Even if you do not store that kind of information on your computer, an attacker who can gain control of your computer may be able to use it in attacks against other people (see Understanding Denial-of-Service Attacks and Understanding Hidden Threats: Rootkits and Botnets for more information).
Myth: Attackers only target people with money. Truth: Anyone can become a victim of identity theft. Attackers look for the biggest reward for the least amount of effort, so they typically target databases that store information about many people. If your information happens to be in the database, it could be collected and used for malicious purposes. It is important to pay attention to your credit information so that you can minimize any potential damage (see Preventing and Responding to Identity Theft for more information).
Myth: When computers slow down, it means that they are old and should be replaced. Truth: It is possible that running newer or larger software programs on an older computer could lead to slow performance, but you may just need to replace or upgrade a particular component (memory, operating system, cd or dvd drive, etc.). Another possibility is that there are other processes or programs running in the background. If your computer has suddenly become slower, you may be experiencing a denial-of-service attack or have spyware on your machine (see Understanding Denial-of-Service Attacks and Recognizing and Avoiding Spyware for more information).
Author: Mindi McDowell
You can find more information from http://www.us-cert.gov/
Debunking Some Common Myths
There are some common myths that may influence your online security practices. Knowing the truth will allow you to make better decisions about how to protect yourself.
How are these myths established?
There is no one cause for these myths. They may have been formed because of a lack of information, an assumption, knowledge of a specific case that was then generalized, or some other source. As with any myth, they are passed from one individual to another, usually because they seem legitimate enough to be true.
Why is it important to know the truth?
While believing these myths may not present a direct threat, they may cause you to be more lax about your security habits. If you are not diligent about protecting yourself, you may be more likely to become a victim of an attack.
What are some common myths, and what is the truth behind them?
Myth: Anti-virus software and firewalls are 100% effective. Truth: Anti-virus software and firewalls are important elements to protecting your information (see Understanding Anti-Virus Software and Understanding Firewalls for more information). However, neither of these elements are guaranteed to protect you from an attack. Combining these technologies with good security habits is the best way to reduce your risk.
Myth: Once software is installed on your computer, you do not have to worry about it anymore. Truth: Vendors may release patches or updated versions of software to address problems or fix vulnerabilities (see Understanding Patches for more information). You should install the patches as soon as possible; some software even offers the option to obtain updates automatically. Making sure that you have the latest virus definitions for your anti-virus software is especially important.
Myth: There is nothing important on your machine, so you do not need to protect it. Truth: Your opinion about what is important may differ from an attacker's opinion. If you have personal or financial data on your computer, attackers may be able to collect it and use it for their own financial gain. Even if you do not store that kind of information on your computer, an attacker who can gain control of your computer may be able to use it in attacks against other people (see Understanding Denial-of-Service Attacks and Understanding Hidden Threats: Rootkits and Botnets for more information).
Myth: Attackers only target people with money. Truth: Anyone can become a victim of identity theft. Attackers look for the biggest reward for the least amount of effort, so they typically target databases that store information about many people. If your information happens to be in the database, it could be collected and used for malicious purposes. It is important to pay attention to your credit information so that you can minimize any potential damage (see Preventing and Responding to Identity Theft for more information).
Myth: When computers slow down, it means that they are old and should be replaced. Truth: It is possible that running newer or larger software programs on an older computer could lead to slow performance, but you may just need to replace or upgrade a particular component (memory, operating system, cd or dvd drive, etc.). Another possibility is that there are other processes or programs running in the background. If your computer has suddenly become slower, you may be experiencing a denial-of-service attack or have spyware on your machine (see Understanding Denial-of-Service Attacks and Recognizing and Avoiding Spyware for more information).
Author: Mindi McDowell
You can find more information from http://www.us-cert.gov/
Wednesday, March 15, 2006
It's 'Official': Windows Vista to Launch in November!
From the "Official Microsoft Connections" event blog we now have an official month for the Vista launch.... November come on down!
read more | digg story
read more | digg story
Tuesday, March 14, 2006
Free downloadable templates NCAA
Microsoft is offering up free downloadable templates for this year’s NCAA men’s and women’s basketball tournaments. The templates are all free, and you can download the tournament brackets for either Excel or Visio.
Trojan Virus Encrypts your files, holds password ransom for $300
A new Trojan identified as CryZip infects files on a computer by encrypting them, then demands a $300 ransom for the password to unlock the files.
A new directory named "AUTO_ZIP_REPORT.TXT" is created with specific instructions on how to use the E-Gold online currency and payment system to send ransom payments.
The instructions, which are marked by misspellings and poor grammar, contain the following text: "Your computer catched our software while browsing illigal porn pages, all your documents, text files, databases was archived with long enought password. You can not guess the password for your archived files - password lenght is more then 10 symbols that makes all password recovery programs fail to bruteforce it (guess password by trying all possible combinations)."
read more | digg story
A new directory named "AUTO_ZIP_REPORT.TXT" is created with specific instructions on how to use the E-Gold online currency and payment system to send ransom payments.
The instructions, which are marked by misspellings and poor grammar, contain the following text: "Your computer catched our software while browsing illigal porn pages, all your documents, text files, databases was archived with long enought password. You can not guess the password for your archived files - password lenght is more then 10 symbols that makes all password recovery programs fail to bruteforce it (guess password by trying all possible combinations)."
read more | digg story
Dell Acquires Alienware
Looks like Dell will be selling AMD systems afterall, through Alienware that is. Reports comfirm the deal has gone down and is closed.
read more | digg story
read more | digg story
Monday, March 13, 2006
21 times more likely to get spyware with IE!
'In May and October, Levy and colleague Steven Gribble sent their crawlers to 45,000 Web sites, cataloged the executable files found, and tested malicious sites' effectiveness by exposing unpatched versions of Internet Explorer and Firefox to drive-by downloads." Here are their results...
read more | digg story
read more | digg story
Firefox is the quickest browser
These tests make it clear that Firefox is the quickest browser, Opera is a bit slower and Internet Explorer is a slowest browser.
read more | digg story
read more | digg story
Protect & Tweak your Registry Tips & Tutorial
Whether you've tweaked your Windows XP setup to the nth degree or have never even emptied your Recycle Bin, there are many ways for you to make Windows work faster, smarter, and safer. All it takes is a willingness to brave the OS's vast repository of settings: the Registry
read more | digg story
read more | digg story
OFFICIAL: Firefox 2.0 Alpha 1 Release This Week!
Firefox 2.0 Alpha 1 is set to be released by the end of this week (in 3 - 4 days), after being delayed a month due to development issues!
read more | digg story
read more | digg story
Saturday, March 11, 2006
Teens and Technology "Is That A Sulky Teenager? No It's A SuperConnector"
I just read an interesting article about Teens and Technology from this Blog
It states that "Technology, it seems, is not isolating teens from each other but quite the opposite: multiplying the number of connections and bonds they make to create a generation of “SuperConnectors”. " Go here to read the rest.
It states that "Technology, it seems, is not isolating teens from each other but quite the opposite: multiplying the number of connections and bonds they make to create a generation of “SuperConnectors”. " Go here to read the rest.
Chess & Online photo editing
My son John A. left at 6am to the KS State Championship at KU in Lawrence today. He has been an avid Chess player for four years now and has a USCF rating of 1195. I hope he does well today. :)
I added Subscribe buttons to this Blog today to make it easer for people to Subscribe using their RSS ( Really Simple Syndication ) readers. Hope this helps. I also added a guest book at the bottom of the page.
Here is a neat online photo editing place. It's called Pixoh.
Pixoh allows a user to upload a photo, or grab it from the web, and edit it online. Currently you can crop, resize and rotate. Then, when you are done, you can save it to your hard drive.
This service is relatively new and very cool. It works great and can be very handy when you don’t have (or don’t want to open) your photo editing software to do basic image edits.
I added Subscribe buttons to this Blog today to make it easer for people to Subscribe using their RSS ( Really Simple Syndication ) readers. Hope this helps. I also added a guest book at the bottom of the page.
Here is a neat online photo editing place. It's called Pixoh.
Pixoh allows a user to upload a photo, or grab it from the web, and edit it online. Currently you can crop, resize and rotate. Then, when you are done, you can save it to your hard drive.
This service is relatively new and very cool. It works great and can be very handy when you don’t have (or don’t want to open) your photo editing software to do basic image edits.
Friday, March 10, 2006
The Story of Ctrl-Alt-Delete
I watched an interesting video this morning and thought I would share it with you. The Story of Ctrl-Alt-Delete Bill Gates does not look to happy. :)
Thursday, March 09, 2006
Want to try Windows Live Messenger?
I installed Windows Live Messenger beta ( Messenger 8 beta ) last night after receiving an invite from Microsoft. I haven't played around with it much yet but did like one new feature. With the new messenger you can send messages to contacts that are offline and they will get them when they sign on. I have a limited number (15) invitations to share for the new Windows Live Messenger beta. They are available on a first-come, first-serve basis and when they're gone, that's it (unless and until Microsoft gives out more of course). If you want in post a comment to this Blog with your e-mail address and I will send you an invite.
System Requirements for Windows Live Messenger
• Multimedia PC
• Pentium 233 MHz process (500 MHz recommended)
• Microsoft Windows XP
• Minimum 128 MB of RAM (256 MB recommended)
• Up to 50 MB of hard disk space for installation, 15 MB to run the program.
• Microsoft Internet Explorer version 6 SP1 or later must be installed on your computer, though it does not need to be your default.
• Minimum 800 x 600 screen resolution
More Info about Windows Live Messenger
http://en.wikipedia.org/wiki/Windows_Live_Messenger
Information on Messenger Plus for Windows Live Messenger
http://www.msgplus.net/news.php
System Requirements for Windows Live Messenger
• Multimedia PC
• Pentium 233 MHz process (500 MHz recommended)
• Microsoft Windows XP
• Minimum 128 MB of RAM (256 MB recommended)
• Up to 50 MB of hard disk space for installation, 15 MB to run the program.
• Microsoft Internet Explorer version 6 SP1 or later must be installed on your computer, though it does not need to be your default.
• Minimum 800 x 600 screen resolution
More Info about Windows Live Messenger
http://en.wikipedia.org/wiki/Windows_Live_Messenger
Information on Messenger Plus for Windows Live Messenger
http://www.msgplus.net/news.php
Wednesday, March 08, 2006
Which version of Windows Vista is right for you?
Good morning, I just woke up and was drinking my morning Coffee and looking through my e-mail and saw my latest e-mail from Microsoft. I thought I would post the contents of that e-mail here.
Which version of Windows Vista is right for you?
People use computers for an unimaginable variety of work and leisure activities. To fit this wide range of uses, Windows Vista will be broadly available in five versions:
For Home:
Windows Vista Home Premium: Goes beyond basic tasks and helps you get more done around the house while more fully enjoying your digital entertainment.
Windows Vista Ultimate: Includes the full set of business, mobility, and home entertainment features for those who use their PCs at work, at home, and on the road.
Windows Vista Home Basic: Increases reliability, security, and ease of use for entry-level computers and basic tasks such as writing e-mail and surfing the Web.
For Business:
Windows Vista Enterprise: Adds protection for sensitive data and helps lower IT costs for large global organizations with highly complex IT infrastructures.
Windows Vista Business: Helps people in organizations of all sizes reduce costs, improve security, increase productivity, and stay better connected.
Which version of Windows Vista is right for you?
People use computers for an unimaginable variety of work and leisure activities. To fit this wide range of uses, Windows Vista will be broadly available in five versions:
For Home:
Windows Vista Home Premium: Goes beyond basic tasks and helps you get more done around the house while more fully enjoying your digital entertainment.
Windows Vista Ultimate: Includes the full set of business, mobility, and home entertainment features for those who use their PCs at work, at home, and on the road.
Windows Vista Home Basic: Increases reliability, security, and ease of use for entry-level computers and basic tasks such as writing e-mail and surfing the Web.
For Business:
Windows Vista Enterprise: Adds protection for sensitive data and helps lower IT costs for large global organizations with highly complex IT infrastructures.
Windows Vista Business: Helps people in organizations of all sizes reduce costs, improve security, increase productivity, and stay better connected.
Tuesday, March 07, 2006
Access your PC from anywhere
Access your PC from anywhere. For seamless access to your PC from anywhere, LogMeIn Pro is the fastest, easiest, most reliable remote access solution available. My son tried it out and it seemed to work great. He was able to control his computer from school. It was interesting to see applications opening and closing and watching the mouse move around his monitor when he was not home.
A free Microsoft tool removes hidden data
Still more information. I thought I would keep along the same subject today, privacy. In case you haven't been keeping up with the latest Tech news you probably don't know that unless you take extra steps, recipients of Word documents can easily see items deleted or modified. A free Microsoft tool removes hidden data from Word, Excel and PowerPoint. The Remove Hidden Data add-in tool (snipurl.com/3osw) will delete hidden text and comments from individual files or a batch of files at once.
From the USAtoday article: For example, how about that letter you sent to Joe Jones? You first referred to him as a "sniveling creep." You changed that to "great guy." But Joe may know what you really think.
From the USAtoday article: For example, how about that letter you sent to Joe Jones? You first referred to him as a "sniveling creep." You changed that to "great guy." But Joe may know what you really think.
IE Privacy Keeper
Here is another nice piece of Free software. It is called IE Privacy Keeper. IE Privacy Keeper automatically cleans up the browser history once you are done surfing the net. The program will correctly clean up all index.dat files without the need for a Windows restart. IE Privacy Keeper will also take care of your offline (system) activity. Opened or deleted documents, viewed pictures and movies, applications run, etc. Take a look.
Macromedia Flash player settings
I have been up for a few hrs. drinking my morning Coffee and reading the news and then thought I would share this info with you. Most people don't realize how much information their computer stores about what they do on the internet.
Here is a link to access your Macromedia Flash player settings. You can go here to Clean up your Flash sites. This takes you to the Settings manager. It is the actual Settings Manager not an image. If you click Delete All Sites, all websites are removed from your list of visited websites. Any information a website may have stored on your computer is erased.
In this panel, you can change storage settings for a website or delete the website so that, if you visit it again, it will use your global settings instead of any individual settings you may have set. You can also delete all sites, which erases any information that may have already been stored on your computer.
Here is a link to access your Macromedia Flash player settings. You can go here to Clean up your Flash sites. This takes you to the Settings manager. It is the actual Settings Manager not an image. If you click Delete All Sites, all websites are removed from your list of visited websites. Any information a website may have stored on your computer is erased.
In this panel, you can change storage settings for a website or delete the website so that, if you visit it again, it will use your global settings instead of any individual settings you may have set. You can also delete all sites, which erases any information that may have already been stored on your computer.
Monday, March 06, 2006
My sons friends show up at dinner time
Yesterday was interesting, I had to try to explain to my 18 year old son that I know more about computers than him. I have been using computers for about 20 years or so. My son just started about 4 years ago. I am not just a casual user, I am a power user. I try to learn everything I can when it comes to this. It is interesting that kids think they know everything. LOL. He has a lot to learn.
I noticed lately that it seems my sons friends show up at dinner time. Last night it was Alex, the night before it was Adam. Of course they ate with us. Maybe they like our cooking. I wonder who it will be next? Last night we had Four Cheese Tortellini with Alfredo Sauce and home made Garlic Bread. Saturday night it was Chicken Kiev with Rice and Corn on the side. I think that tonight will be make your own dinner night. :) Now, if I could just get my son to think that he knows more about cooking than me I would be all set. I would never have to cook again. I think he can make a toasted cheese sandwich, and I know for a fact he can make hotdogs in the microwave. Hotdogs are about the only thing we see him cook. I wonder what he will eat when he is out on his own? :)
I noticed lately that it seems my sons friends show up at dinner time. Last night it was Alex, the night before it was Adam. Of course they ate with us. Maybe they like our cooking. I wonder who it will be next? Last night we had Four Cheese Tortellini with Alfredo Sauce and home made Garlic Bread. Saturday night it was Chicken Kiev with Rice and Corn on the side. I think that tonight will be make your own dinner night. :) Now, if I could just get my son to think that he knows more about cooking than me I would be all set. I would never have to cook again. I think he can make a toasted cheese sandwich, and I know for a fact he can make hotdogs in the microwave. Hotdogs are about the only thing we see him cook. I wonder what he will eat when he is out on his own? :)
Sunday, March 05, 2006
Free USB Drive
Anyone want a free USB drive? If you go to this website and click on the ad for the USB Drive where it says "Valuable Information - Get Yours".
You get one free from Microsoft.. John
You get one free from Microsoft.. John
Saturday, March 04, 2006
Why Mac Computers Suck
Here is a great video on why Mac Computers Suck...
http://geeksaresexy.blogspot.com/2006/03/why-mac-computers-suck.html
http://geeksaresexy.blogspot.com/2006/03/why-mac-computers-suck.html
Alternative user interface
My Desktop This Morning
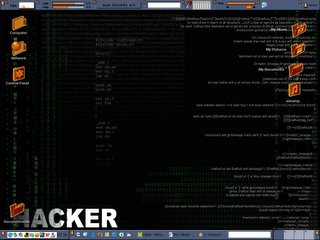
I finally found a good replacement for WindowBlinds. It's called SharpE. SharpE is an alternative user interface for use with any modern Windows operating system (Windows 2K/XP/2K3). It replaces the Windows shell. (A shell is a program that interfaces directly with the user on one side and with underlying operating system functions on the other side.)
http://www.sharpe-shell.org/news.php
Friday, March 03, 2006
We can't wait for summer to get here
It's afternoon now. All the bills are paid, oh what fun. We can't wait for summer to get here. The gas prices are killing us with the gas heat in the house. It doesn't help that this house is over 100 years old with no insulation in the exterior walls. I guess it's the same everywhere so I shouldn't complain too much. One of these days we will have it insulated. One thing at a time. :) That's all for now.
Paying Bills and Drinking Coffee

Not much going on today. It's Friday and I have to go pay bills and get stuff from the store. Just started on my second pot of coffee for the day. :) Taste good. My wife bought me this creamer that taste great. I can't stand black coffee. Sorry all. But have always liked it lite and sweet. I did add my Blogroll from Bloglines to this blog today. That's all for now.
Thursday, March 02, 2006
You Know You’ve Had Too Much Caffeine When…
My Dad is home and is doing well. The Dr's won't let him play golf for two weeks and he will have to keep an eye on things from now on but aside from that he is fine for now. Thank God. As I sat here drinking my coffee ( need that morning caffeine ) I read the news on my Bloglines. I came across this, it's kinda funny and I wanted to share it. John
You Know You’ve Had Too Much Caffeine When…
You might be a caffeine addict if:
Your web page has the Mountain Dew color scheme.
You don’t sweat, you percolate.
You have to drink some form of caffeinated beverage just to sleep.
Your eyes stay open when you sneeze.
You lick your coffeepot clean.
You know from experience caffeine tablets don’t dissolve in cola.
Juan Valdez names his donkey after you.
You grind your coffee beans in your mouth.
You get a speeding ticket even when you’re parked
You can jump-start your car without cables.
You see nothing wrong with using water joe to make the coffee you use to take your no-doze.
You want to be cremated just so you can spend eternity in a coffee can.
The dishes in your house are all coffee cups.
Starbuck’s owns the mortgage on your house.
You suck on a used coffee filter and grounds whenever the can runs out of coffee.
You have distilled Jolt Cola to make it more potent.
A cup of coffee before bed doesn’t keep you from falling asleep anymore.
You’ve worn out the handle on your favorite coffee mug.
You’ve ever used the airplane’s call button just to get a coffee refill.
You dip espresso beans.
You slip into a coma if you drink decaf by accident.
You’ve given up sex, TV, and all forms of meat for Lent before, but STILL can’t make it 40 days without caffeine.
Your birthday is a national holiday in Colombia.
You go to AA meetings just for the free coffee.
You go to the doctor because you’re afraid there might be blood in your Mountain Dew stream.
You can name the five flavors of JOLT.
You need a caffeinated beverage after lunch to avoid being cranky all afternoon.
You believe that the coffee bean is a vegetable.
You have a website about caffeine.
You Know You’ve Had Too Much Caffeine When…
You might be a caffeine addict if:
Your web page has the Mountain Dew color scheme.
You don’t sweat, you percolate.
You have to drink some form of caffeinated beverage just to sleep.
Your eyes stay open when you sneeze.
You lick your coffeepot clean.
You know from experience caffeine tablets don’t dissolve in cola.
Juan Valdez names his donkey after you.
You grind your coffee beans in your mouth.
You get a speeding ticket even when you’re parked
You can jump-start your car without cables.
You see nothing wrong with using water joe to make the coffee you use to take your no-doze.
You want to be cremated just so you can spend eternity in a coffee can.
The dishes in your house are all coffee cups.
Starbuck’s owns the mortgage on your house.
You suck on a used coffee filter and grounds whenever the can runs out of coffee.
You have distilled Jolt Cola to make it more potent.
A cup of coffee before bed doesn’t keep you from falling asleep anymore.
You’ve worn out the handle on your favorite coffee mug.
You’ve ever used the airplane’s call button just to get a coffee refill.
You dip espresso beans.
You slip into a coma if you drink decaf by accident.
You’ve given up sex, TV, and all forms of meat for Lent before, but STILL can’t make it 40 days without caffeine.
Your birthday is a national holiday in Colombia.
You go to AA meetings just for the free coffee.
You go to the doctor because you’re afraid there might be blood in your Mountain Dew stream.
You can name the five flavors of JOLT.
You need a caffeinated beverage after lunch to avoid being cranky all afternoon.
You believe that the coffee bean is a vegetable.
You have a website about caffeine.
Subscribe to:
Comments (Atom)